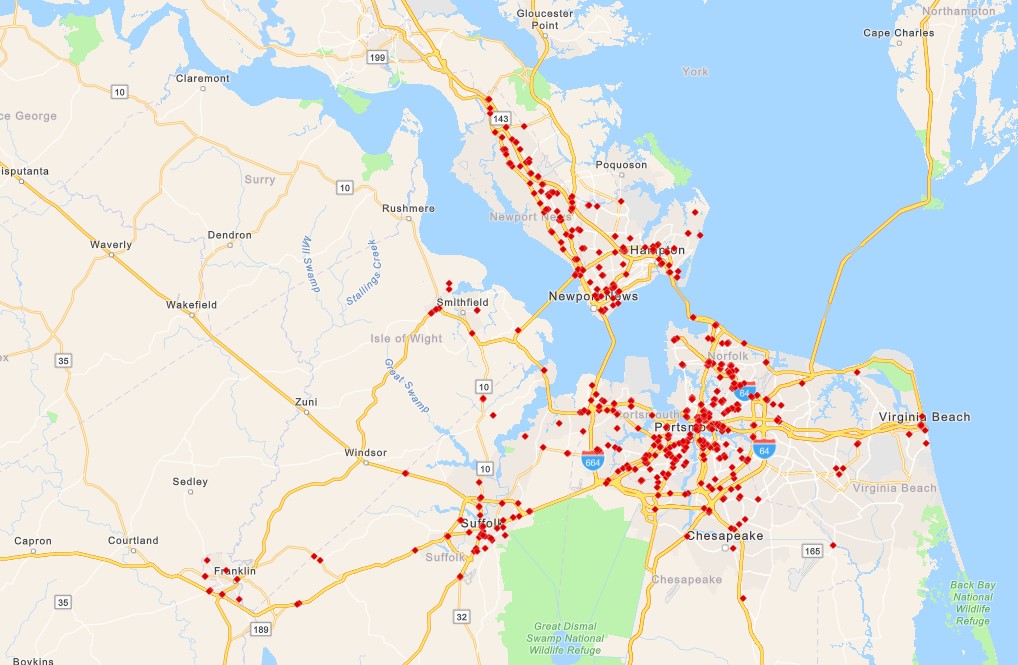
A Norfolk federal judge released the locations of more than 600 Flock Safety surveillance cameras in Hampton Roads the first time such a compilation has been made public.
Tag: infrastructure
TLDRs: SoftBank shares fall 6. 6% as Asian chip sector reacts to Nvidia’s modest US drop. SK Hynix, Samsung, and TSMC also see sharp declines following Nvidia market reaction. AI server demand and GPU orders remain strong despite short-term selloff pressures. ABF substrate capacity and advanced packaging could shape 2025 semiconductor growth. SoftBank Group Corp. (SFTBY) [.] The post SoftBank (SFTBY) Stock Slides 6. 6% Amid Chip Sector Selloff appeared first on CoinCentral.
Global Commercial Building Acoustic Panel Market demonstrates robust growth, with its valuation reaching USD 15. 2 billion in 2024. According to comprehensive industry analysis, the market is projected to expand at a strong CAGR of 7. 1%, potentially reaching USD 25. 8 billion by 2032.
Trump Set To Meet With ‘Communist Mayor of New York City’
Firefighters extinguished a small fire near Realization Point in Boulder on Tuesday evening, and they have determined it was not sparked by natural causes or electrical infrastructure.
Saif Ali Khan makes major real estate move; buys commercial offices worth Rs. 30.75 crores in Mumbai

Bollywood actor Saif Ali Khan has added yet another prime asset to his real estate portfolio, this time in Mumbai’s thriving commercial district of Andheri East. According to property registration documents, the actor has purchased two office units in the Kanakia Wallstreet building for a total consideration of Rs. 30. 75 crore. The combined area of the newly acquired offices measures 5, 681 sq ft and includes six dedicated parking spaces. The seller of the property is Apiore Pharmaceutical, a US-based pharma company, as reflected in the registration filings. The deal was arranged by Volney, a real estate advisory and investor network firm. The transaction was officially registered on November 18, 2025, with a stamp duty of Rs. 1. 84 crore and a registration fee of Rs. 60, 000. Industry experts note that Andheri East has rapidly emerged as one of Mumbai’s busiest commercial corridors, attracting corporates, global enterprises, and creative firms due to its improved connectivity and infrastructure. Volney’s founder, Rohan Sheth, described the area as a market that combines accessibility with strong rental prospects, adding that it continues to draw long-term investors. Saif’s new commercial investment also places him among several high-profile names who have recently secured space in the vicinity. Elon Musk’s satellite internet company, Starlink Satellite Communications Private Limited, recently leased a 1, 294 sq. ft. office in the nearby Chandivali area for a five-year period, with total rent valued at Rs. 2. 33 crore. Additionally, the same building previously housed leased offices where Hrithik Roshan and Rakesh Roshan acquired three commercial units earlier this year for about Rs. 31 crores through HRX Digitech LLP. Beyond his latest acquisition, Saif Ali Khan is already known for his premium residential and commercial holdings across Mumbai. He currently resides in a high-end apartment in Bandra West, a property he purchased nearly a decade ago for Rs. 24 crores. Records also show that he bought a sprawling 6, 500 sq. ft. apartment in April 2012 for Rs. 23. 50 crore from Satguru Builders, further cementing his presence in the city’s luxury real estate landscape. With his latest investment, the actor continues to strengthen his position not just in cinema but also in Mumbai’s top-tier property market. Also Read: Dining with the Kapoors Trailer: Netflix brings together Bollywood’s first family for a grand tribute to Raj Kapoor.
The post FanHub Revolutionizes Sports Fandom Economy with Avalanche Blockchain appeared com. Felix Pinkston Nov 18, 2025 02: 16 FanHub introduces a decentralized platform using Avalanche blockchain to transform sports fandom into a dynamic economy, providing tangible rewards and opportunities for fans and businesses. FanHub, a pioneering platform in the Fantech space, is set to revolutionize the sports fandom landscape by leveraging decentralized technology. According to Avax. network, this innovative platform aims to create an organic economy where new value flows are established between fans, teams, and brands. The Broken Traditional Model For over a century, the sports business model has seen little evolution, with fans contributing passion and money primarily benefiting broadcasters and social platforms. Traditional sponsorships focus on brand awareness without clear ROI, often excluding smaller businesses. FanHub seeks to disrupt this model by turning fan engagement into a transaction layer that offers tangible rewards, democratizing access for smaller businesses. Addressing Fan Needs Fans often seek recognition and tangible benefits, yet the current system provides little in return. Traditional sponsorships are costly and designed for large brands, leaving small and midsized businesses at a disadvantage. FanHub addresses these issues with a mobile-first, gamified app that generates economic value from fan interactions. Features include match check-ins, lineup predictions, and fan stats, all verified on the Avalanche blockchain. Innovative Offerings FanHub rewards users with LYLTY Points, redeemable for a variety of incentives such as free merchandise, partner discounts, and soon, vouchers with major food delivery apps. Businesses can also join as LYLTY Partners, allowing them to offer loyalty rewards to customers without upfront costs. This infrastructure has been approved by major financial institutions like Visa, Mastercard, and American Express, ensuring a seamless user experience. Expanding Market Reach The platform targets a vast £0. 5 trillion market encompassing sports betting, sponsorship, and fan travel. FanHub has strategically focused.
Cebu, Philippines When we first reported on Meta Earth’s “From E to Emergency” campaign, it was a fascinating question: could a Web3 project offer . Read more.
TLDR CoreWeave stock fell nearly 30% over five trading days after cutting 2025 revenue guidance from $5. 25 billion to $5. 1 billion The company reported a backlog of $55. 6 billion in Q3, up 85% from the prior quarter, including major contracts with OpenAI and Meta Despite the pullback, shares remain up over 108% year-to-date on strong [.] The post CoreWeave (CRWV) Stock Drops 30% Despite Winning Major Contracts From OpenAI and Meta appeared first on CoinCentral.
The post Pepe’s Madness, Hyperliquid’s Speed, & Ethereum Classic’s Code Meet Their Match in BlockDAG’s $435M+ Presale appeared com. Crypto Presales Compare BlockDAG, Hyperliquid, Pepe, and Ethereum Classic as the best crypto projects disrupting markets with speed, community power, and conviction-driven blockchain principles The world of digital currency is currently a chaos of noise and staggering wealth. Yet, a few projects manage to break through, demanding attention with verifiable activity, surging community power, or immense funding. This report dives into the four best crypto projects that are sparking debate across the market. These projects span the extreme range of the digital economy. They include BlockDAG, Pepe, Hyperliquid and Ethereum Classic. Each project presents a completely different thesis. The objective here is not to forecast future outcomes. Instead, we dissect the core factors that force these coins into every serious conversation about the best crypto projects right now. 1. BlockDAG: The New Challenger to Legacy Networks BlockDAG (BDAG) has become a symbol of massive market confidence before even hitting public exchanges. The project’s launch success is undeniable. It has already raised $435 million+ and attracted over 312, 000 holders. BlockDAG uses a hybrid model. It takes Bitcoin’s Proof-of-Work for security and merges it with a Directed Acyclic Graph (DAG) system for speed. This architecture promises blazing speeds, aiming for 2, 000 to 15, 000 transactions per second (TPS). This is not just a whitepaper fantasy; the Awakening Testnet is running. It currently processes over 1, 400+ TPS and fully supports applications built for Ethereum. The participation is visible and real. The X-Series miners, which generate between 200 to 2, 000 BDAG coins daily, are already deployed globally. Over 20, 000 mining units have been sold. This shows tangible adoption beyond mere passive holding. The leadership team, which includes experts like CEO Antony Turner and advisor Dr. Maurice Herlihy, adds institutional weight. The presale is ending fast. Coins are currently at $0. 005 in Batch 32. With 4. 2.